Before we know how to prevent, we should also understand how they attack first. Here’s how some of the typical Telegram scams play out:
- Phishing attacks: A Telegram user poses as someone you’d otherwise trust (such as a friend, colleague, or a customer support agent) to trick you into giving up your personal information. For example, Attacker created a similar telegram account with different username to ask you to send screenshot or your information.
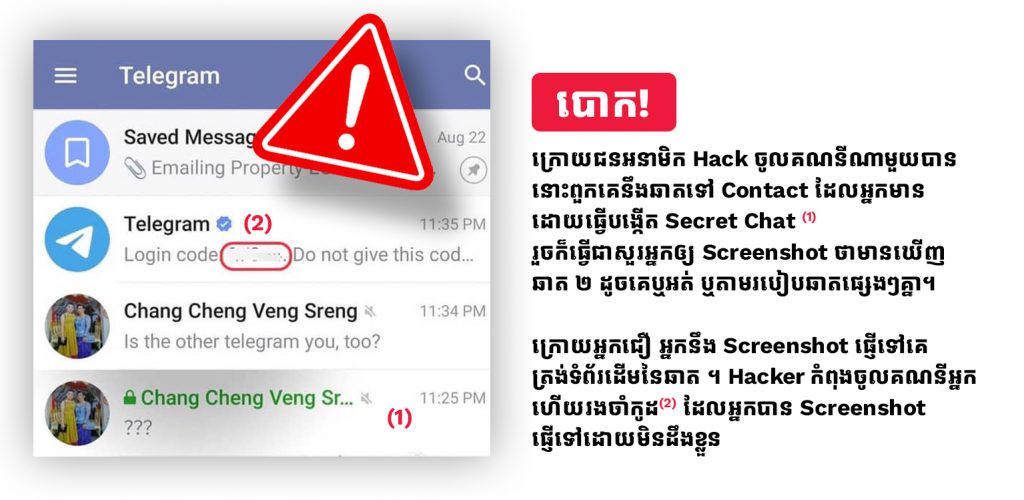
- Off-platform scams: Someone sends you a link or convinces you to go off the Telegram platform and onto a less-secure site. This site could be used to steal your personal information or even infect your device with malware.
- Telegram bot attacks: The Telegram platform allows users to create bot accounts, which scammers use to rapidly target vulnerable legitimate accounts. A bot known as X-Files can steal passwords, session cookies, login credentials, and credit card details according to Intel 471 research released in July 2022.
- Crypto scams: Telegram has become the go-to platform for people interested in cryptocurrencies and blockchain. Many cybercriminals target Telegram users to get access to their crypto wallets, and transfer out their bitcoin (BTC), Ethereum, and other coins. This may not be most common scam since Crypto is not widely opened in Cambodia.
How to protect your account?
First thing first, Check your SIM Card ID registration. Is it registered with SIM card providers? Since Telegram is using phone number to register, hence SIM swap attacks is also common, which transfer ownership of your phone number to a malicious attacker, are a common attack vector.

SIM REGISTRATION CHECK
For example: You did not register the SIM card properly but just made unknown ID purchase for signup Telegram. Once SIM expired, it will be sold publicly.
And once the attacker has your number in hand, they can cause all sorts of mayhem, most notably by obtaining two-factor authentication (2FA) codes for your important logins that are sent over text.
In dept prevention:
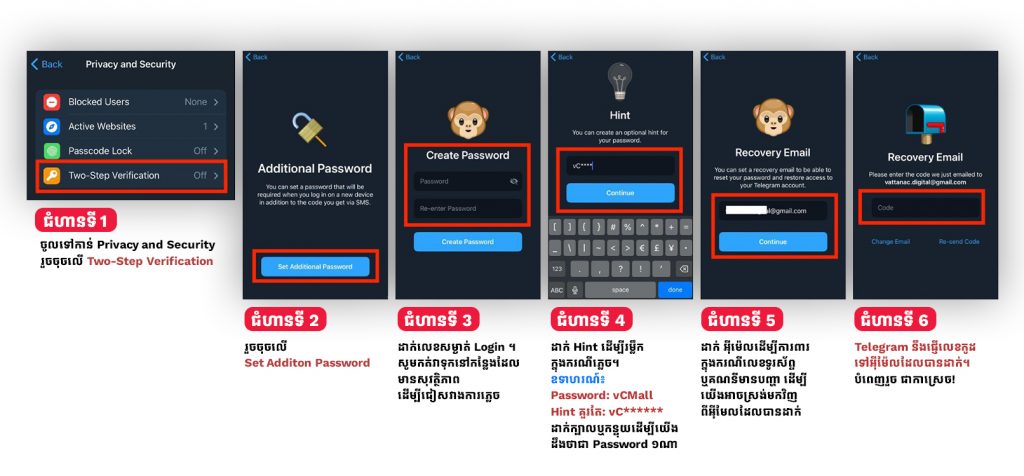
1. Set up 2-Factor Authentication
Set up two-factor authentication to protect your account against hijacking. The primary login method uses a one-time code sent by text, so Telegram lets you set a password as the second factor.
In case someone manages to SIM swap you, Telegram will prompt them for a password in order to access your account, instead of just letting them in based on having access to the phone number.
To do so, on the Privacy and Security tab, select Two-Step Verification (Telegram’s term for 2FA), and set a strong combination. You will rarely enter this password in, so make sure that you store it somewhere safe, like in a password manager, so you won’t forget it.
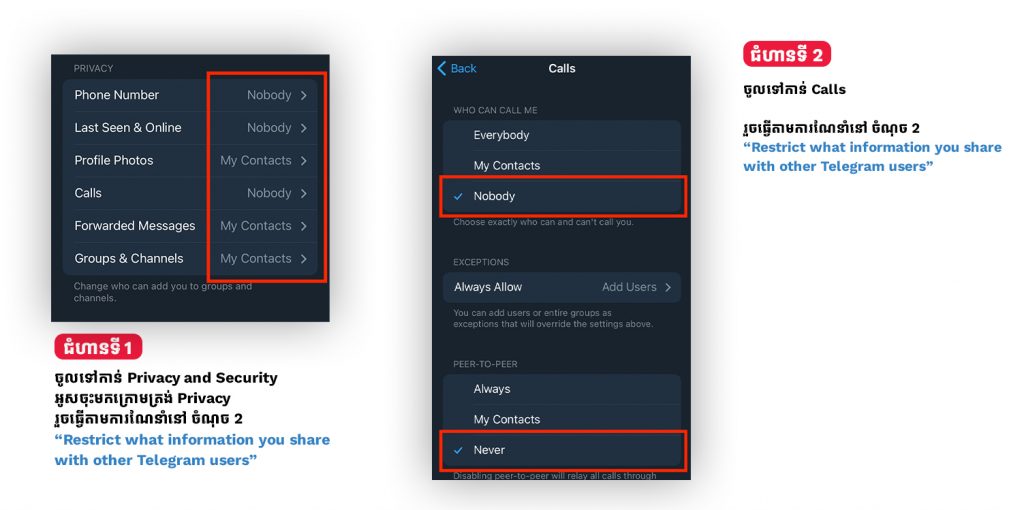
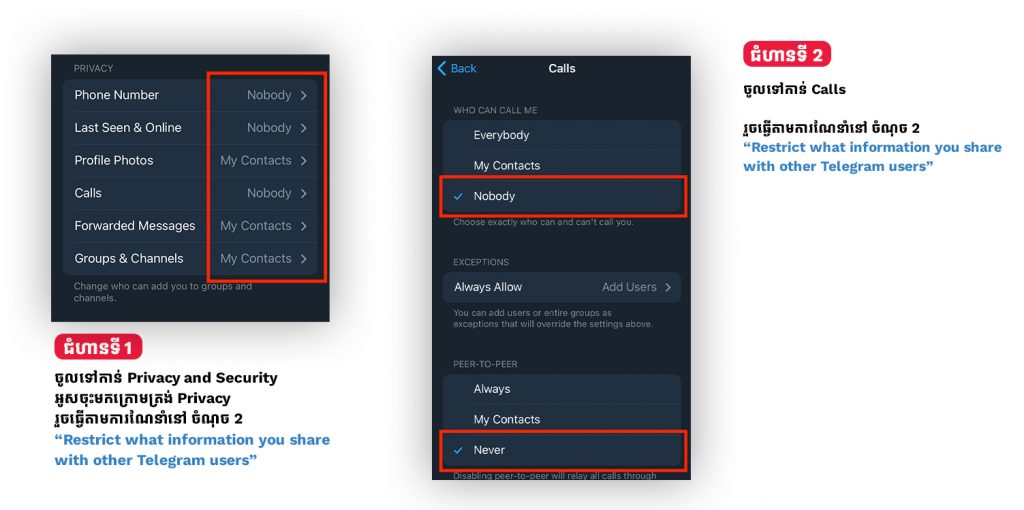
2. Restrict what information you share with other Telegram users
So as not to share unnecessary details with all 500 million Telegram users, you need to configure your profile privacy appropriately. Go to Telegram’s Privacy settings. We recommend the following:
Phone Number → Who can see my phone number — Nobody.
Phone Number → Who can find me by my number — My Contacts.
Last Seen & Online → Who can see my timestamp — Nobody.
Profile photo → Who can see my profile photo — My Contacts.
Calls → Who can call me — My Contacts (or Nobody, if you prefer).
Calls→ Peer-to-peer — My contacts (or Nobody, if you prefer not to share your IP address with chat partners).
Forwarded Messages → Who can add a link to my account when forwarding my messages — My Contacts.
Groups & Channels → Who can add me — My Contacts.
3. Modify data download and storage settings
On your mobile version of Telegram,
navigate over to Privacy & Security → Data Settings and remove from Telegram storage any information you do not want to be there.
This also good to remove if someone sent us a malware executable software.
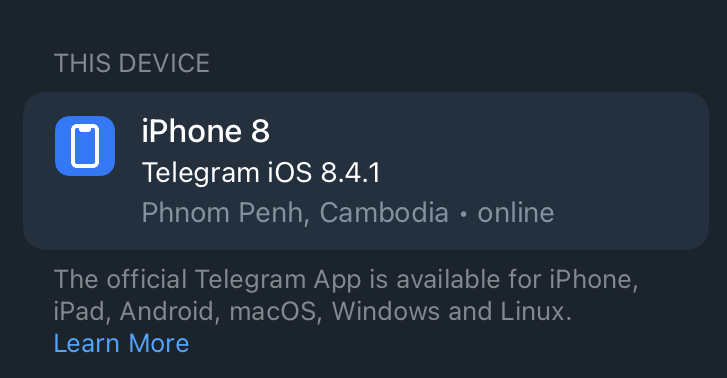
4. Check active sessions
From our last solved cases in our company, I found out that the attacker is one person who attack continuously through the contact you have. From my notice, Attacker have logged in to accounts longer than 6 hours before they have activities because by default Telegram won’t allow new logged in user who logged in less than 6 hours to terminate other session. So, check your Active Session more often.
To do this, go to Settings → Privacy and Security → Active sessions.
If you see any session that is still logged in that you want to be ended, simply click on that session and hit ‘Terminate’ to end it.
5. Disable P2P calls for everyone
You can prevent IP addresses from being compromised by changing settings. Go to Settings: Private and Security → Voice Call → Peer-to-Peer to Never or Nobody.
With this setup, the user will need to make a voice call through the Telegram server, although the IP address is hidden.
6. Don’t open executable files or click link from other users

Some hackers just use Telegram as a method of communication with their potential victims, rather than attacking any features inherent to Telegram itself. For example, some hackers create a similar user with your contact to send you the malware software or link and ask you to click on it then you’ll get infected by open their insecure website link or software.
7. Watch out for impersonation

It’s extremely common for hackers and scammers to impersonate Telegram users by choosing a username, profile picture that is very close to, but slightly different from, the original. For example, an attacker may try to impersonate vattanaccampitalmall by creating the username vattanacmall. Make sure you know who you’re communicating with.